A hash in blockchain is a unique alphanumeric string generated through a cryptographic algorithm from transaction data. It functions as a “digital fingerprint” that uniquely identifies transaction information. This hash value, far from being a mere label, plays a crucial role in preserving the integrity and security of the information. Why is this so vital? The answer lies in the intrinsic nature of the hash: any modification to the original data will result in a completely different hash.
History and Origins of the Hash Function
The concept of hash functions, as a means of uniquely summarizing data, has its foundations in the evolution of computing and cryptography throughout history. While the idea of condensing information into unique codes is as old as writing itself, the early glimpses of what we now know as modern hash functions emerged in the 1950s and 1960s.
The Era of Mainframe Computers:
- In the 1950s and 1960s, with the advent of mainframe computers, computer scientists explored more efficient ways to manage and manipulate large sets of data.
- Hash functions found their early purposes in data management, enabling swift search and retrieval of information in emerging computational environments.
Developments in Cryptography:
- As modern cryptography began to take shape, hash functions found a new purpose in data security.
- The seminal work of Merkle-Damgård in the 1970s laid the groundwork for the construction of cryptographic hash functions, emphasizing their importance in information security.
MD5 and SHA-1: The Rise of Hash Algorithms:
- In the 1990s, MD5 (Message Digest Algorithm 5) and SHA-1 (Secure Hash Algorithm 1) became the most widely used hash algorithms.
- MD5, despite its initial popularity, proved vulnerable to collisions, leading to the development of more secure algorithms like SHA-2.
Continuous Evolution with SHA-2 and SHA-3:
- SHA-2, released in 2001, introduced more secure variants resistant to attacks.
- SHA-3, selected in 2012, stood out for its sponge-based design, offering a robust and novel alternative.
Towards the Future: Current Developments and Emerging Trends:
- Present times witness a focus on quantum-resistant and adaptive hash algorithms as quantum computing advances.
- Projects like BLAKE3 are exploring more efficient and faster implementations to meet the demands of growing digital complexity.
How a Hash Works in the Context of Blockchain
In the blockchain ecosystem, the role of the hash is crucial for ensuring the immutability and authenticity of transactions. When a transaction is initiated, essential data such as sender identification, recipient, and transferred amount undergo a specific hash algorithm.
This algorithm, often based on secure cryptographic functions, generates a unique hash that serves as a kind of “digital signature” for the transaction in question. This hash becomes a unique identifier, encapsulating all relevant transaction information in an apparently random alphanumeric string.
The real magic happens when this hash is incorporated into the block of the chain. Each block contains not only the details of the transaction itself but also the hash of the previous block. This method of chaining, from one block to the next, creates a structure called the “blockchain.” In this process, the hash of each block depends on the content of the previous block and the block itself, creating an unbreakable link between all blocks in the chain.
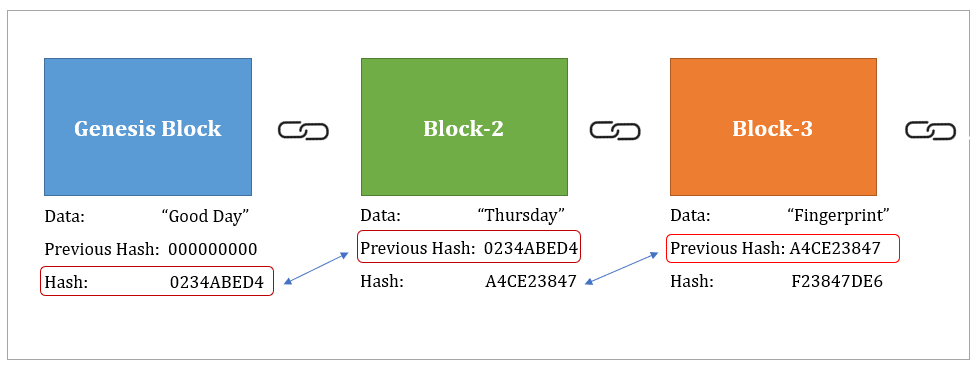
Immutability of the Blockchain and Resistance to Manipulation
The sequential connection of blocks through hashes has significant implications for security in blockchain. If someone attempts to modify the data of a transaction in a specific block, the associated hash will change completely. Since this hash is part of the next block and so on, any alteration attempt would affect not only the block in question but the entire blockchain.
This interconnection feature makes tampering with a transaction extremely difficult and detectable. For an attacker to change a transaction, they would have to recalculate the hash of that block and all subsequent blocks. In a decentralized network, where multiple participants maintain copies of the chain, detecting such manipulation becomes practically impossible, providing an additional layer of security and reliability in blockchain transactions.
Irreversibility of the Hash: Absolute Protection
At the heart of blockchain security and digital transactions lies the crucial property of irreversibility associated with hashes. Irreversibility implies that once the original data of a transaction has been turned into a hash, it is impossible to reconstruct the original data from the hash. This principle is essential for safeguarding the integrity of information and protecting against manipulation attempts.
When a hash is generated from transaction data, any change, even the slightest, in that data will generate a completely different hash. The irreversibility of the process prevents an attacker from working backward, i.e., starting from the hash to reach the original data. This aspect is fundamental to prevent unauthorized alterations in the information stored in the blockchain.
Practical Illustration:
To illustrate this property, let’s imagine a transaction on the blockchain as a masterpiece painting. The original transaction data is like the unique brushstrokes composing the painting. The resulting hash, in this case, would be akin to taking a photograph of the complete painting. If someone tries to alter even a single stroke of the painting, the resulting photograph, or hash, will change drastically.
Let’s assume someone attempts to modify the amount of cryptocurrency transferred in a transaction. By doing so, they alter the original data and, consequently, generate a new hash. However, since the hash is linked to the block and affects all subsequent blocks, the network will immediately detect the discrepancy between the stored hash and the recalculated one. This early detection and the inability to reverse the hash to the original data act as an inflexible shield against malicious manipulation.
Enhancing Overall Security:
The irreversibility of the hash is not just a technical feature but a solid foundation for trust in transactions. By ensuring that each change generates a new, unique, and irreversible hash, a robust barrier is established against information corruption in a decentralized environment. This feature not only reinforces blockchain security but also strengthens trust in the integrity of digital transactions in the vast and evolving landscape of emerging technologies.
Hashes in Smart Contracts: Secure Automation
The integration of hash functions in smart contracts represents a significant advancement in automation and security within the blockchain ecosystem. These contracts, essential for the execution of decentralized agreements, leverage the unique property of hashes to ensure integrity and seamless execution of predefined conditions.
Within a smart contract, there is a need to verify and enforce agreed-upon conditions. Hashes come into play by uniquely and securely representing the terms and details of the contract. By generating a hash from these conditions, any alteration in the contract would result in a drastic change in the hash, thus alerting the network to potential manipulations.
Practical Examples:
- Identity Verification:
- In smart contracts involving financial transactions, hashes are used to ensure the identity of the parties involved. Identity information can be hashed and stored on the blockchain, providing a secure and private method of verification.
- Payment Condition:
- In contracts involving payments, a hash of the amount and payment conditions is stored on the blockchain. When the specified conditions are met, the contract is automatically executed, releasing the payment securely and without the need for intermediaries.
- Supply Chain Management:
- In contracts related to the supply chain, hashes can represent chain details, such as product origin or delivery date. Any change in these details will generate a new hash, ensuring transparency and integrity of information.
The history and application of hash functions in blockchain reveal an essential tool that has evolved to play a fundamental role in the security, integrity, and efficiency of digital transactions.








